Contents
禅道 弱口令分析
<!–more–>
正文
默认配置
http://192.168.198.133/zentao/admin-safe.html
默认配置的禅道会要求管理员登陆后修改弱口令。
密码密文的计算方式
hashTable.md5(hashTable.md5(this.plaintext)+this.salt)
$('#loginPanel #submit').click(function()
{
var password = $('input:password').val().trim();
var passwordStrength = computePasswordStrength(password);
$('#submit').after("<input type='hidden' name='passwordStrength' value='" + passwordStrength + "'>");
var rand = $('input#verifyRand').val();
if(password.length != 32 && typeof(md5) == 'function') $('input:password').val(md5(md5(password) + rand));
});
登陆成功
请求
POST /zentao/user-login.html HTTP/1.1
Host: 192.168.198.133
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
Connection: close
Referer: http://192.168.198.133/zentao/user-login.html
Cookie: lang=zh-cn; device=desktop; theme=default; windowWidth=1600; windowHeight=800; zentaosid=t3csarc01dtp45jutkcsr6d2v4
Upgrade-Insecure-Requests: 1
account=admin&password=ed0fadfd4d585a845b7d0a484611fcc7&passwordStrength=1&verifyRand=919862299
响应
HTTP/1.1 200 OK
Date: Mon, 16 Sep 2019 05:07:31 GMT
Server: Apache
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: private
Pragma: no-cache
Set-Cookie: lang=zh-cn; expires=Wed, 16-Oct-2019 05:07:31 GMT; Max-Age=2592000; path=/zentao/
Set-Cookie: device=desktop; expires=Wed, 16-Oct-2019 05:07:31 GMT; Max-Age=2592000; path=/zentao/
Set-Cookie: theme=default; expires=Wed, 16-Oct-2019 05:07:31 GMT; Max-Age=2592000; path=/zentao/
Vary: Accept-Encoding
Content-Length: 123
Connection: close
Content-Type: text/html; Language=UTF-8;charset=UTF-8
<html><meta charset='utf-8'/><style>body{background:white}</style><script>parent.location='/zentao/index.html';
</script>
登陆失败
请求
POST /zentao/user-login.html HTTP/1.1
Host: 192.168.198.133
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
Connection: close
Referer: http://192.168.198.133/zentao/user-login.html
Cookie: lang=zh-cn; device=desktop; theme=default; windowWidth=1473; windowHeight=790; zentaosid=t3csarc01dtp45jutkcsr6d2v4
Upgrade-Insecure-Requests: 1
account=admin&password=7706abfdcfc8aa09c705b69b726ac51e&passwordStrength=0&verifyRand=331530951
响应
HTTP/1.1 200 OK
Date: Mon, 16 Sep 2019 05:08:36 GMT
Server: Apache
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: private
Pragma: no-cache
Set-Cookie: lang=zh-cn; expires=Wed, 16-Oct-2019 05:08:36 GMT; Max-Age=2592000; path=/zentao/
Set-Cookie: device=desktop; expires=Wed, 16-Oct-2019 05:08:36 GMT; Max-Age=2592000; path=/zentao/
Set-Cookie: theme=default; expires=Wed, 16-Oct-2019 05:08:36 GMT; Max-Age=2592000; path=/zentao/
Vary: Accept-Encoding
Content-Length: 254
Connection: close
Content-Type: text/html; Language=UTF-8;charset=UTF-8
<html><meta charset='utf-8'/><style>body{background:white}</style><script>alert('您还有3次尝试机会。')
</script>
<html><meta charset='utf-8'/><style>body{background:white}</style><script>if(window.parent) window.parent.$.enableForm();
</script>
逆向登陆流程
观察登陆过程
通过页面 http://192.168.198.133/zentao/index.php?m=user&f=login 采用相同的用户名、密码以及 Cookie 登陆,但拦截的 HTTP 请求不同,尤其是登陆密码哈希后的值不同。
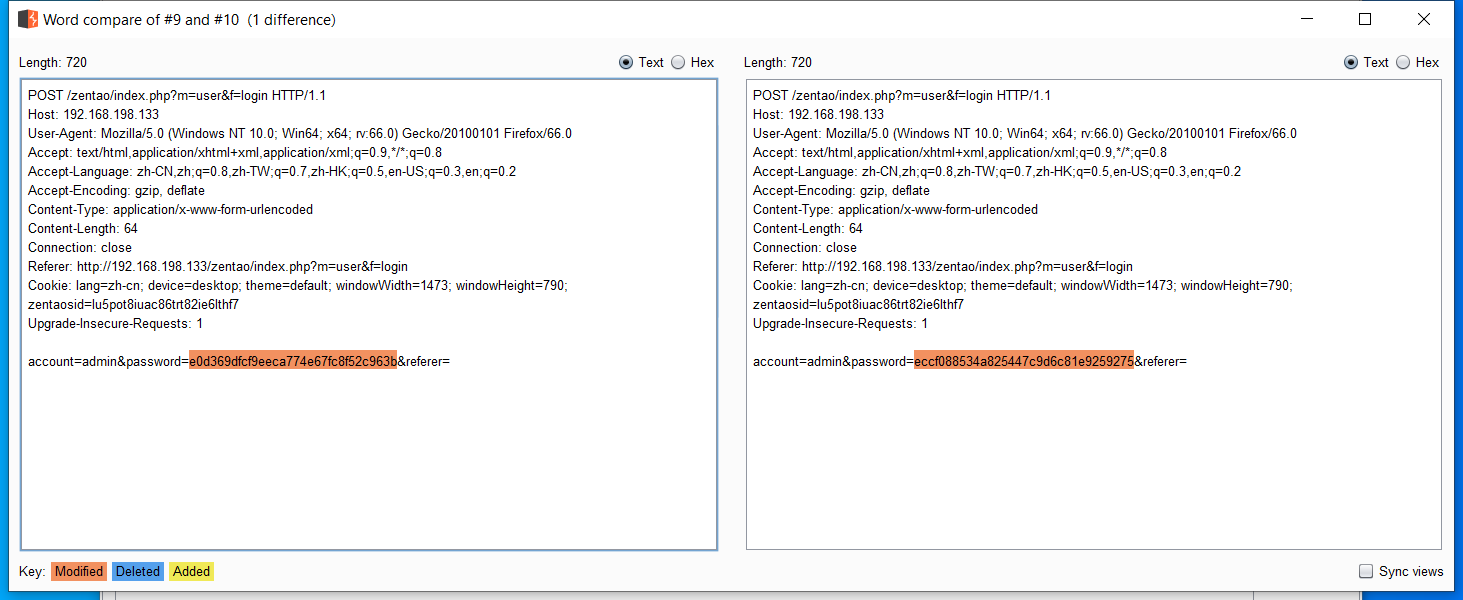
跟踪登陆按钮的 click 事件监听器
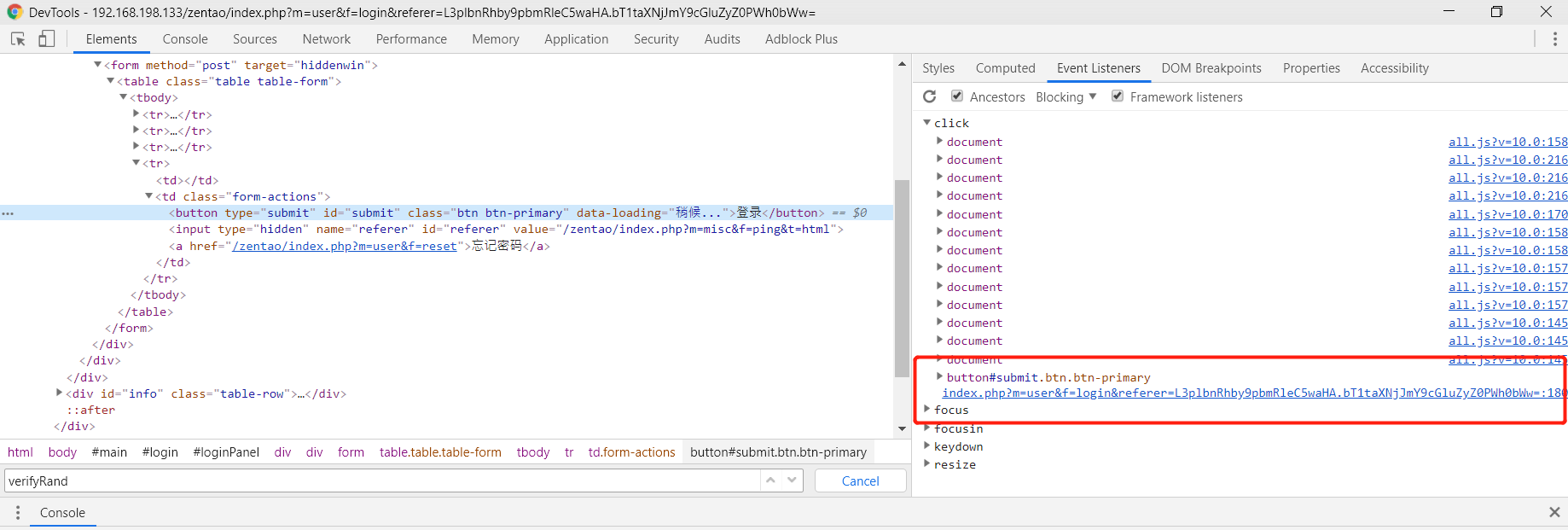
发现一段关键的 JavaScript 。
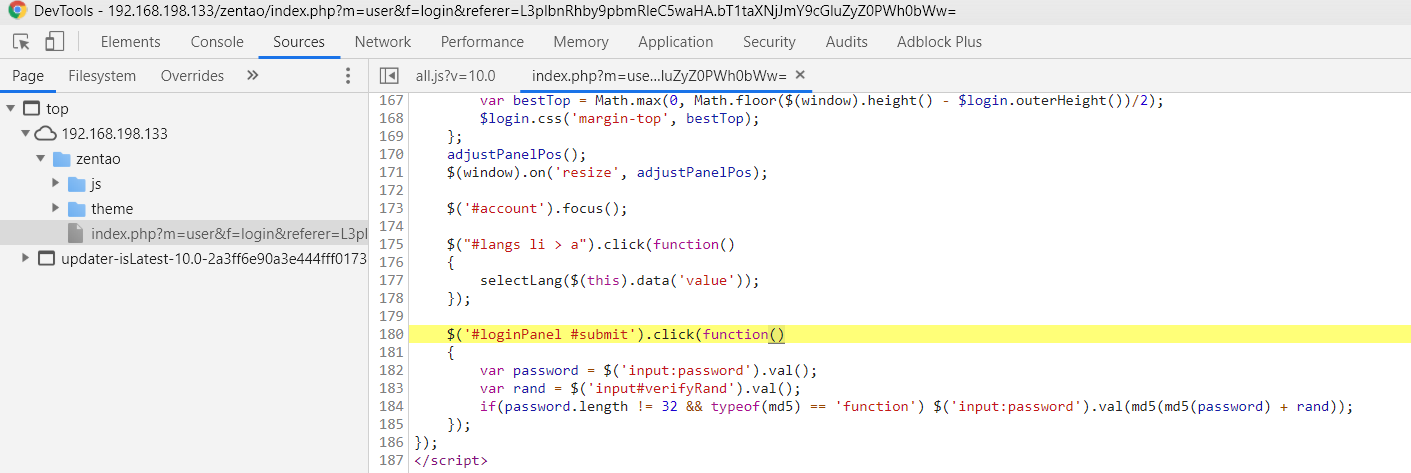
阅读该函数,通过一定猜测,推测大致流程如下:
在客户端第一期 GET 请求登陆页面 http://192.168.198.133/zentao/index.php?m=user&f=login 时,服务端返回的 HTTP 响应中包含一个隐藏的 input 表单 <input type="hidden" name="verifyRand" id="verifyRand" value="1529845456"> ,该表单的 verifyRand 值在服务端与 跟踪用户身份的 Cookie 绑定,最终通过类似 hashTable.md5(hashTable.md5(this.password)+this.verifyRand) 的机制计算出最终的密码哈希。
zentao_weakpass.go
Leave a Reply