Contents
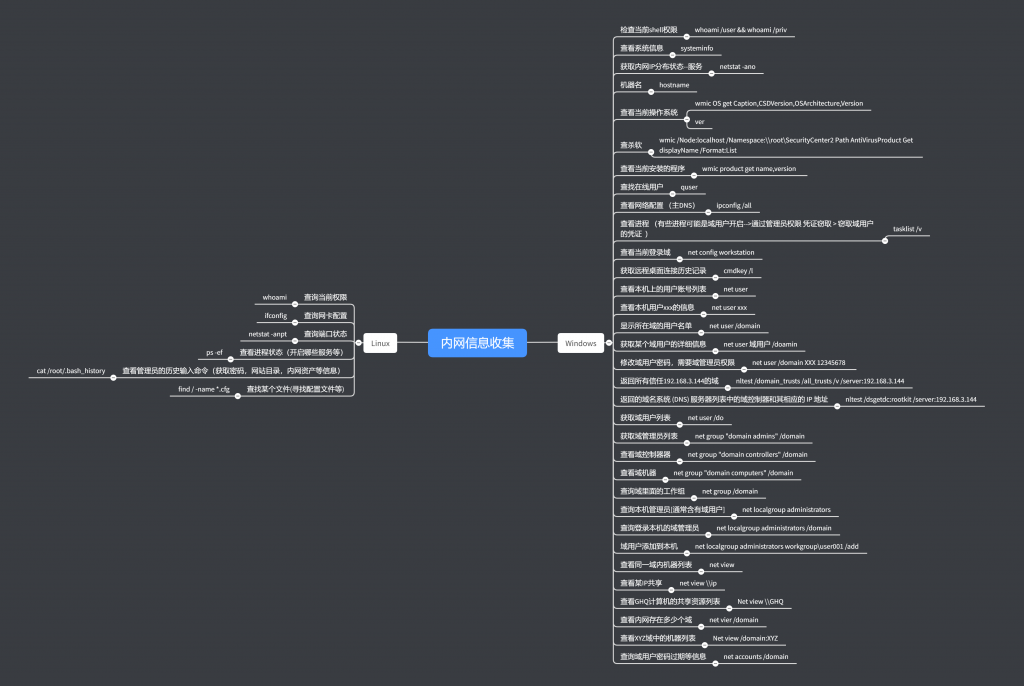
内网主机信息收集 (Windows)
判断是否在 域 中
net time /domain
检查当前 shell 的用户权限
# cmd
whoami /user && whoami /priv
wmic USERACCOUNT get Caption,Name,PasswordRequired,Status
# powershell
whoami -user; whoami -priv
wmic USERACCOUNT get Caption,Name,PasswordRequired,Status
查看当前系统基本信息
# cmd & powershell
systeminfo
获取内网主机/IP/服务状态
当前主机的网络连接情况
# cmd & powershell
netstat -ano
# Get Information About NICs
> wmic NIC get Description,MACAddress,NetEnabled,Speed
Description MACAddress NetEnabled Speed
WAN Miniport (SSTP)
WAN Miniport (L2TP)
WAN Miniport (PPTP) 50:50:54:22:11:00
WAN Miniport (PPPOE) 33:50:6F:22:11:00
WAN Miniport (IPv6)
WAN Miniport (Network Monitor)
Microsoft ISATAP Adapter 100000
WAN Miniport (IP)
Microsoft Tun Miniport Adapter 02:00:54:22:11:00 1073741824
RedHat PV NIC Driver 02:9B:9F:22:11:00 TRUE 100000000
RAS Async Adapter 20:41:53:22:11:00
获取主机名信息
# cmd & powershell
hostname
获取系统版本信息
# cmd
wmic /?
wmic OS get /?
wmic OS get Caption, CSDVersion, OSArchitecture, Version
ver
# powershell
echo $psversiontable # powershell 版本
[System.Environment]::OSVersion.Version
wmic OS get Caption,CSDVersion,OSArchitecture,Version
# https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-wmiobject?view=powershell-5.1
(Get-WmiObject -class Win32_OperatingSystem).Caption
(Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").ReleaseId
wmic 其他操作
# 基本操作
wmic <alias> list <brief|full>
wmic OS list /?
wmic OS list brief
wmic OS list full
wmic CPU list brief
wmic CPU list full
# 导出成文件
wmic baseboard list /format /?
wmic baseboard list /format:HTABLE > D:\output.html
wmic baseboard list /format:XML > D:\output.xml
# 导出到剪贴板
wmic baseboard list brief /format:list | clip
# Get Information About Physical Drives 磁盘信息
> wmic DISKDRIVE get InterfaceType,Name,Size,Status
InterfaceType Name Size Status
SCSI \\.\PHYSICALDRIVE0 85896599040 OK
SCSI \\.\PHYSICALDRIVE1 107372805120 OK
SCSI \\.\PHYSICALDRIVE2 10733990400 OK
SCSI \\.\PHYSICALDRIVE3 85896599040 OK
SCSI \\.\PHYSICALDRIVE4 85896599040 OK
# Get Serial Numbers of Hard Drives 磁盘序列号
> wmic path win32_physicalmedia get SerialNumber
SerialNumber
9RXFA3FG
Z2AP14Z2
# Get Memory Device DIMM Numbers
> wmic MEMORYCHIP get Capacity,DeviceLocator,PartNumber,Tag
Capacity DeviceLocator PartNumber Tag
2147483648 DIMM_A2 HMT325R7BFR8A-H9 Physical Memory 1
2147483648 DIMM_A3 HMT325R7BFR8A-H9 Physical Memory 2
2147483648 DIMM_A5 HMT325R7BFR8A-H9 Physical Memory 4
2147483648 DIMM_A6 HMT325R7BFR8A-H9 Physical Memory 5
8589934592 DIMM_A8 9965516-099.A00LF Physical Memory 7
8589934592 DIMM_A9 9965516-099.A00LF Physical Memory 8
2147483648 DIMM_B2 HMT325R7BFR8A-H9 Physical Memory 10
2147483648 DIMM_B3 HMT325R7BFR8A-H9 Physical Memory 11
2147483648 DIMM_B5 HMT325R7BFR8A-H9 Physical Memory 13
2147483648 DIMM_B6 HMT325R7BFR8A-H9 Physical Memory 14
8589934592 DIMM_B8 9965516-099.A00LF Physical Memory 16
8589934592 DIMM_B9 9965516-099.A00LF Physical Memory 17
# Get Information About CPU
> wmic CPU get Name,NumberOfCores,NumberOfLogicalProcessors
Name NumberOfCores NumberOfLogicalProcessors
Intel(R) Xeon(R) CPU E5-2665 0 @ 2.40GHz 2 2
# Get Information About BIOS
> wmic BIOS get Manufacturer,Name,SMBIOSBIOSVersion,Version
Manufacturer Name SMBIOSBIOSVersion Version
Xen Revision: 1.221 3.4.3.amazon Xen - 0
查找系统安装的杀毒软件
wmic /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct get /format:LIST
查看当前安装的程序
wmic product list brief
wmic product get name,version
查看当前在线的用户
# cmd & powersh
quser
查看网络配置 (主DNS)
ipconfig /all
# powershell
ipconfig -all
查看进程
有些进程可能是域用户它通过窃取域管理员凭据开启。
# bash & powershell
tasklist /v
查看当前登陆域
net config workstation
获取远程桌面连接过的历史账户列表
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/cmdkey
cmdkey /list
查看本地用户账号列表
# 查看本地用户账号列表
net user
# 查看用户详细信息
net user <username>
域用户信息
# 显示所在域的用户名单
net user /domain
# 获取某个域用户的详细信息
net user <username> /domain
# 修改域用户密码 (需要域管理员权限)
net user /domain <username> <new_password>
# 返回所有 信任 192.168.3.144 的域
nltest /domain_trust /all_trusts /v /server:192.168.3.144
# 返回 DNS 服务器列表中的域控制器和其对应IP的地址
nltest /dsgetdc:rootkit /server:192.168.3.144
# 获取域管理员列表
net group "doamin admins" /domain
# 查看域控制器
net group "domain controllers" /domain
# 查看域里面的工作组
net group /domain
# 查询本机的管理员(通常含有域用户)
net localgroup administrators
# 查询登陆本机的域管理员
net localgroup administrators /domain
# 将域用户添加到本机
net localgroup administrators workgroup\user001 /add
# 查看同一域内机器列表
net view
# 查看某个主机的共享文件
net view \\<ip_address>
# 查看 GHQ (主机名) 计算器的共享资源列表
net view \\GHQ
# 查看内网中存在多少个域
net view /domain
# 查看 域 XYZ 中的机器列表
net view /domain:XYZ
# 查询域用户密码过期等信息
net accounts /domain
Poershell 中的 wmic
http://acidx.net/wordpress/2012/09/retrieving-system-information-via-command-line-on-windows/
Get-WmiObject -Query "Select * From Win32_Service Where State='Running'" | Format-Table Name,Description,ProcessId
Get-WmiObject -List -Namespace "root\cimv2" | Sort
自动化脚本
http://wp.blkstone.me/2019/12/domain-info-gathering-automation/
参考资料
Get Windows System Information via WMI Command-line (WMIC)
https://www.lisenet.com/2014/get-windows-system-information-via-wmi-command-line-wmic/
Retrieving System Information via Command Line on Windows
http://acidx.net/wordpress/2012/09/retrieving-system-information-via-command-line-on-windows/
Leave a Reply