Nmap 的一些用法整理 / Nmap Cheat Sheet v1.1
Contents
Nmap 架构图
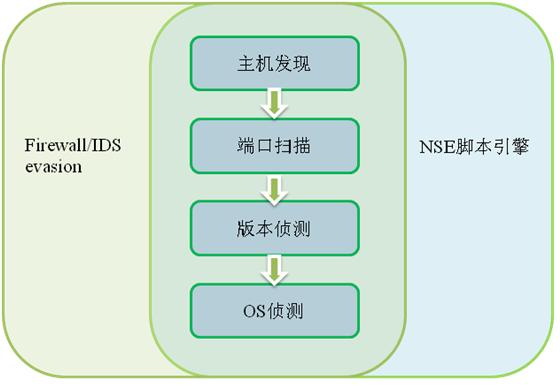
正文
#
#
# 统计大范围扫描的端口开放情况
grep " open " ms-vscan.nmap | sed -r 's/ +/ /g' | sort | uniq -c | sort -rn | less
# 全功能扫描
nmap -A -T4 scanme.nmap.org
# nse 脚本示例
# -d 提供调试脚本的 debug 信息
nmap -n -Pn -p 80 --open --script http-webcam -oN webcam.nmap [-d] 192.168.1.1/24
# 主机发现
nmap -T4 -n -f -vvv --reason -PE -PP -PM -PS21,22,23,25,80,443,113,31339,11389 -PA80,113,443,10042 --top-port 50 192.168.1.1/24
nmap -T4 -n -vvv --reason -PE -PP [-PM] [-PU] [-PO] -PS21,22,23,25,80,443,113,31339,11389 -PA80,113,443,10042 -sS [-sT] --top-port 50 -O --osscan-limit -sV --version-intensity 2 --script http-server-header, http-title 192.168.1.1/24
nmap [-n] -sS -PE -PP [-PM] -PS21,22,23,25,80,443,113,31339 -PA80,113,443,10042 -PU -PO --source-port 53 -T4 --reason 192.168.1.1/24
nmap -vvv --packet-trace -PO -top-port 5 scanme.nmap.org
nmap -vvv [-n] -Pn -sT -p80 --packet-trace --source-port 53 --reason scanme.nmap.org
nmap -vvv [-n] -Pn -sS -p80 --packet-trace --source-port 53 --reason scanme.nmap.org
# 轻量级服务探测与重量级服务探测
nmap -Pn -n -vvv -sV --version-all --open --top-port 100 192.168.1.1
nmap -Pn -n -vvv -sV --version-light --open --top-port 100 192.168.1.1
# HTTP 轻量漏扫
nmap --script "http-vuln*" 192.168.1.1
# ms
nmap -T4 --top-ports 50 -sV -O --osscan-guess --min-hostgroup 128 --host-timeout 10m -oA ms-vscan -iL ms.ips.lst
# smb info
nmap -n -Pn -v -O -sT -sV -T4 -oA ms-smbscan --script=smb-enum-domains,smb-enum-processes,smb-enum-sessions,smb-enum-shares,smb-enum-users,smb-os-discovery,smb-security-mode,smb-system-info scanme.nmap.org
# Nmap display Netbios name
nmap -sU --script nbstat.nse -p 137 target
# Nmap check if Netbios servers are vulnerable to MS08-067
# 注意 使用 unsafe=1 的参数可能导致远程主机崩溃(crash)
nmap --script-args=unsafe=1 --script smb-check-vulns.nse -p 445 target
# MAC 地址伪造
# -f, -ff 碎片包 用于绕过防火墙 https://nmap.org/book/man-bypass-firewalls-ids.html
nmap -vvv -f -Pn --host-time 10n --spoof-mac Cisco -PE -n -p- -iL ip.txt -oG bt.txt
# XML 输出参考
nmap -sS -sV -T5 10.0.1.99 --webxml -oX - | xsltproc --output file.html -
# nmap 与 nikto 组合使用
# Scans for http servers on port 80 and pipes into Nikto for scanning.
nmap -p80 10.0.1.0/24 -oG - | nikto.pl -h -
# Scans for http/https servers on port 80, 443 and pipes into Nikto for scanning.
nmap -p80,443 10.0.1.0/24 -oG - | nikto.pl -h -
# dns discovery
nmap -n -vvv -Pn -sU -p 5353 --sciprt "dns-service-discovery" <target_ip>
# 当你在防火墙前面时 最好不要一次性扫描大量端口,容易被防火墙规则命中
nmap -vvv -n -ff -Pn -sS --top-port 50 cds.zt-express.com
https://nmap.org/book/man.html
https://nmap.org/book/man-host-discovery.html
详细解释一下主机发现的脚本
-n 是不进行反向 DNS 查询,可以加快扫描速度。
-vvv 更多的输出信息
-PE -PP -PM 基于 ICMP echo, timestamp, netmask 的扫描。 建议后两者二选一。
-PS 空的 带 SYN flag 的 TCP 包 (empty TCP packet with the SYN flag set)
-PA 空的 带 ACK flag 的 TCP 包 (empty TCP packet with the ACK flag set)
–source-port 固定源端口,用于穿透防火墙
-T 4 带拥塞控制的速度调节,4为默认值,5为最大值。
–reason 给出 Nmap 判断端口状态的理由 syn-ack, rst, or no-response.
–packet-trace 查看发出的与接收的 IP packet 的详细信息
关于加快扫描速度的几个建议
-sV –version-light 轻量级 version deteciton
-n 不进行反向 DNS 查询
其他 tip
使用 --spoof-mac 可能导致结果不一致。
# A best nmap scan strategy for networks of all sizes
# Host Discovery - Generate Live Hosts List
$ nmap -sn -T4 -oG Discovery.gnmap 192.168.56.0/24
$ grep "Status: Up" Discovery.gnmap | cut -f 2 -d ' ' > LiveHosts.txt
# Port Discovery - Most Common Ports
# http://nmap.org/presentations/BHDC08/bhdc08-slides-fyodor.pdf
$ nmap -sS -T4 -Pn -oG TopTCP -iL LiveHosts.txt
$ nmap -sU -T4 -Pn -oN TopUDP -iL LiveHosts.txt
$ nmap -sS -T4 -Pn --top-ports 3674 -oG 3674 -iL LiveHosts.txt
# Port Discovery - Full Port Scans (UDP is very slow)
$ nmap -sS -T4 -Pn -p 0-65535 -oN FullTCP -iL LiveHosts.txt
$ nmap -sU -T4 -Pn -p 0-65535 -oN FullUDP -iL LiveHosts.txt
# Print TCP\UDP Ports
$ grep "open" FullTCP|cut -f 1 -d ' ' | sort -nu | cut -f 1 -d '/' |xargs | sed 's/ /,/g'|awk '{print "T:"$0}'
$ grep "open" FullUDP|cut -f 1 -d ' ' | sort -nu | cut -f 1 -d '/' |xargs | sed 's/ /,/g'|awk '{print "U:"$0}'
# Detect Service Version
$ nmap -sV -T4 -Pn -oG ServiceDetect -iL LiveHosts.txt
# Operating System Scan
$ nmap -O -T4 -Pn -oG OSDetect -iL LiveHosts.txt
# OS and Service Detect
$ nmap -O -sV -T4 -Pn -p U:53,111,137,T:21-25,80,139,8080 -oG OS_Service_Detect -iL LiveHosts.txt
常用 Nmap 脚本
# smb
# http
http-server-header
http-title
http-vuln*
http-iis-short-name-brute
http-iis-webdav-vuln
http-methods
http-php-version
http-phpmyadmin-dir-traversal
http-put
http-robots.txt
http-security-headers
http-shellshock
http-trace
http-vhosts
http-waf-detect
http-waf-fingerprint
http-webdav-scan
# misc
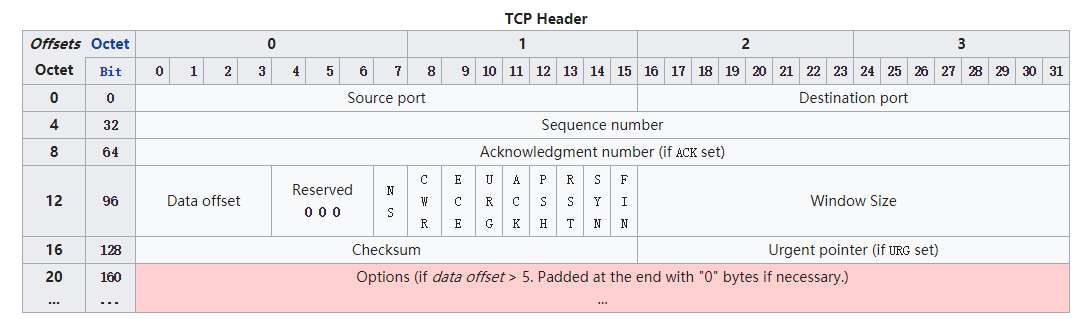
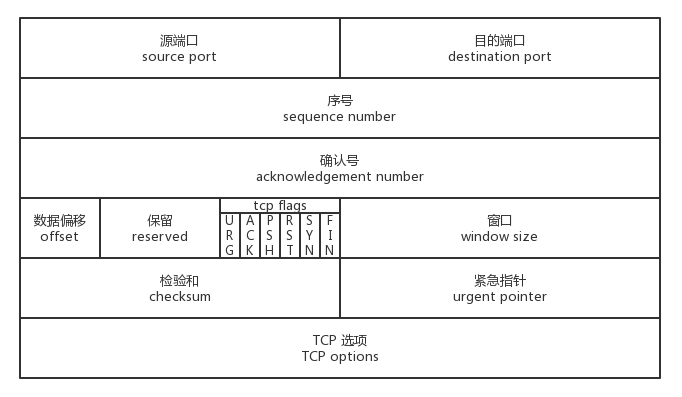
TCP 报文结构
https://en.wikipedia.org/wiki/Transmission_Control_Protocol
https://jerryc8080.gitbooks.io/understand-tcp-and-udp/chapter2.html
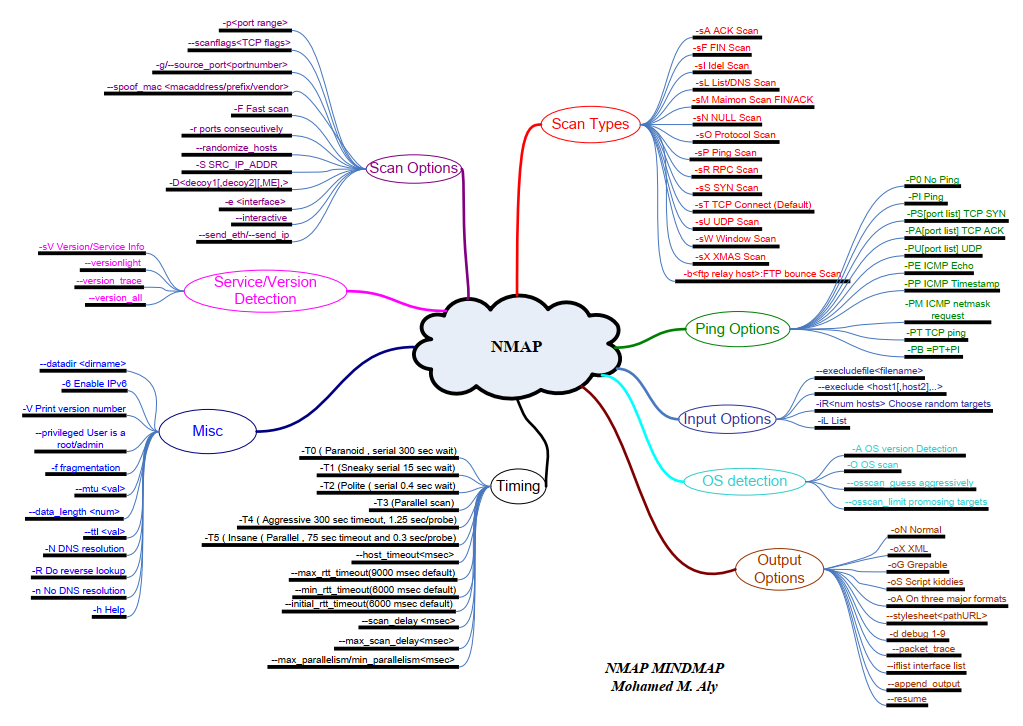
Nmap 选项思维导图
https://nanshihui.github.io/2017/03/29/zmap%E6%BA%90%E7%A0%81%E8%A7%A3%E8%AF%BB%E4%B9%8Bzmap%E6%89%AB%E6%8F%8F%E5%BF%AB%E7%9A%84%E5%8E%9F%E5%9B%A0/
常见端口
常见内网端口与服务整理
| 序号 | 端口 | 协议 | 服务名称 | 备注 |
| 1 | 20 | TCP | FTP | |
| 2 | 21 | TCP | FTP | |
| 3 | 22 | TCP | SSH | |
| 4 | 23 | TCP | Telnet | |
| 5 | 25 | TCP | SMTP | |
| 6 | 37 | TCP | TIME protocol | |
| 7 | 53 | TCP | DNS | |
| 8 | 69 | TCP | TFTP | |
| 9 | 80 | TCP | HTTP/Apache/Tomcat | |
| 10 | 81 | TCP | HTTP/IIS/ipcam | |
| 11 | 82 | TCP | HTTP | |
| 12 | 83 | TCP | HTTP | |
| 13 | 88 | TCP | Keberos | |
| 14 | 110 | TCP | SMTP | |
| 15 | 113 | TCP | auth | |
| 16 | 135 | TCP | RPC/SMB | |
| 17 | 137 | TCP | NetBIOS Name Service | |
| 18 | 138 | TCP | NetBIOS Datagram Service | |
| 19 | 139 | TCP | Samba-文件与打印共享 | |
| 20 | 143 | TCP | IMAP4 | |
| 21 | 161 | TCP | SNMP | |
| 22 | 162 | TCP | SNMP | |
| 23 | 383 | TCP | HP OpenView HTTPs Operations Agent | |
| 24 | 389 | TCP | LDAP | |
| 25 | 443 | TCP | HTTPS | |
| 26 | 445 | TCP | Microsoft-DS (Active Directory, Windows shares) | |
| 27 | 464 | TCP | Keberos | |
| 28 | 546 | TCP | DHCPv6 client | |
| 29 | 547 | TCP | DHCPv6 server | |
| 30 | 554 | TCP | rtsp | |
| 31 | 636 | TCP | LDAP over SSL | |
| 32 | 749 | TCP | Keberos | |
| 33 | 808 | TCP | ||
| 34 | 873 | TCP | Rsync | |
| 35 | 902 | TCP | VMware ESXi | |
| 36 | 981 | TCP | Remote HTTPS management for firewall devices running embedded Check Point VPN-1 software | |
| 37 | 987 | TCP | VMware ESXi | |
| 38 | 1058 | TCP | nim, IBM AIX Network Installation Manager (NIM) | |
| 39 | 1059 | TCP | nimreg, IBM AIX Network Installation Manager (NIM) | |
| 40 | 1080 | TCP | Shadowsocks | |
| 41 | 1194 | TCP | OpenVPN | |
| 42 | 1433 | TCP | SQLServer/MSSQL | |
| 43 | 1521 | TCP | Oracle | |
| 44 | 1589 | TCP | Cisco VLAN Query Protocol (VQP) | |
| 45 | 1998 | TCP | Cisco X.25 over TCP (XOT) service | |
| 46 | 2000 | TCP | Cisco Skinny Client Control Protocol (SCCP) | |
| 47 | 2049 | TCP | Network File System (NFS) | |
| 48 | 2181 | TCP | Zookeeper | |
| 49 | 2375 | TCP | Docker | |
| 50 | 3306 | TCP | MySQL | |
| 51 | 3389 | TCP | MS-RDP | |
| 52 | 4000 | TCP | NodeJS | |
| 53 | 4899 | TCP | Radmin | |
| 54 | 5000 | TCP | Python Flask | |
| 55 | 5432 | TCP | PostgreSQL | |
| 56 | 5631 | TCP | Symantec/PCAnywhere | |
| 57 | 5632 | TCP | PCAnywhere | |
| 58 | 5900 | TCP | VNC | |
| 59 | 5901 | TCP | VNC | |
| 60 | 5902 | TCP | VNC | |
| 61 | 6080 | TCP | ||
| 62 | 6379 | TCP | Redis | |
| 63 | 7001 | TCP | Weblogic | |
| 64 | 7002 | TCP | Weblogic | |
| 65 | 7018 | TCP | Weblogic | |
| 66 | 7077 | TCP | Weblogic | |
| 67 | 7288 | TCP | Weblogic | |
| 68 | 7990 | TCP | Atlassian Bitbucket | |
| 69 | 8012 | TCP | ||
| 70 | 8014 | TCP | ||
| 71 | 8020 | TCP | HDFS | |
| 72 | 8030 | TCP | ||
| 73 | 8031 | TCP | YARN | |
| 74 | 8032 | TCP | YARN | |
| 75 | 8055 | TCP | HTTP | |
| 76 | 8080 | TCP | Resin/HTTP/GlassFish | |
| 77 | 8081 | TCP | HTTP | |
| 78 | 8082 | TCP | ||
| 79 | 8088 | TCP | YARN | |
| 80 | 8089 | TCP | Jenkins | |
| 81 | 8090 | TCP | Atlassian Confluence | |
| 82 | 8118 | TCP | Privoxy—advertisement-filtering Web proxy | |
| 83 | 8120 | TCP | ||
| 84 | 8139 | TCP | Puppet (software) Client agent | |
| 85 | 8140 | TCP | Puppet (software) Master server | |
| 86 | 8161 | TCP | ActiveMQ/Apache Group | |
| 87 | 8332 | TCP | Bitcoin JSON-RPC server | |
| 88 | 8333 | TCP | Bitcoin/Vmware | |
| 89 | 8433 | TCP | HTTPS/VPN | |
| 90 | 8443 | TCP | HTTPS/VPN | |
| 91 | 8649 | TCP | Ganglia | |
| 92 | 8888 | TCP | HTTP | |
| 93 | 8983 | TCP | ||
| 94 | 9001 | TCP | Supervisor | |
| 95 | 9043 | TCP | Websphere | |
| 96 | 9060 | TCP | WebSphere Application Server Administration Console | |
| 97 | 9090 | TCP | Hbase | |
| 98 | 9092 | TCP | Kafka | |
| 99 | 9095 | TCP | Hbase | |
| 100 | 9200 | TCP | ElasticSearch | |
| 101 | 9300 | TCP | ElasticSearch | |
| 102 | 9989 | TCP | HTTP | |
| 103 | 9990 | TCP | Jboss | |
| 104 | 10050 | TCP | Zabbix agent | |
| 105 | 10051 | TCP | Zabbix trapper | |
| 106 | 11211 | TCP | Memcached | |
| 107 | 11389 | TCP | MS-RDP | |
| 108 | 14001 | TCP | HTTP | |
| 109 | 17001 | TCP | Weblogic | |
| 110 | 17002 | TCP | Weblogic | |
| 111 | 17077 | TCP | Weblogic | |
| 112 | 20880 | TCP | dubbo | |
| 113 | 22350 | TCP | ||
| 114 | 27017 | TCP | MongoDB | |
| 115 | 27018 | TCP | MongoDB | |
| 116 | 27019 | TCP | MongoDB | |
| 117 | 28017 | TCP | MongoDB | |
| 118 | 50010 | TCP | HDFS DataNode | |
| 119 | 50070 | TCP | HDFS | |
| 120 | 50075 | TCP | HDFS DataNode HTTP | |
| 121 | 60000 | TCP | Hbase | |
| 122 | 60010 | TCP | Hbase | |
| 123 | 60020 | TCP | Hbase | |
| 124 | 60030 | TCP | Hbase | |
| 1 | 53 | UDP | domain | |
| 2 | 67 | UDP | dhcps | |
| 3 | 123 | UDP | ntp | |
| 4 | 135 | UDP | msrpc | |
| 5 | 137 | UDP | netbios-ns | |
| 6 | 138 | UDP | netbios-dgm | |
| 7 | 139 | UDP | netbios-ssn | |
| 8 | 161 | UDP | snmp | |
| 9 | 445 | UDP | microsoft-ds | |
| 10 | 1434 | UDP | ms-sql-m |
其他参考资料
Nmap Cheat Sheet
https://highon.coffee/blog/nmap-cheat-sheet/
渗透测试工具备忘录
https://xz.aliyun.com/t/2482
Penetration Testing Tools Cheat Sheet
https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
Pentest Tips and Tricks #1
https://jivoi.github.io/2015/07/01/pentest-tips-and-tricks/
Pentest Tips and Tricks #2
A best nmap scan strategy for networks of all sizes
https://jivoi.github.io/2015/08/21/pentest-tips-and-tricks-number-2/
Nmap 在实战中的高级用法
http://www.03sec.com/1859.shtml
Refining Your Nmap Scan Strategy By Tony Lee
http://securitysynapse.blogspot.com/2013/08/refining-your-nmap-scan-strategy.html
Leave a Reply